Developing usable secure systems in the context of a developing nation like India is a big challenge. Our goal is to understand the way users use secure systems and use this understanding to develop technologies which will get adopted in real-world.
Current Projects:
- SMSAssassin: Detecting SMS spams using crowd sourcing approach
- ChaMAILeon: Simplified email sharing like never before!
Past Projects:
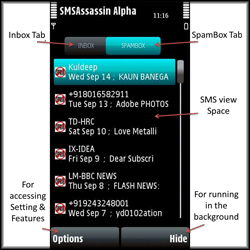 Due to exponential increase in use of Short Message Service (SMS) over mobile phones in developing countries, there has been a burst of spam SMSes. The main goal for this research is to build algorithms and solutions to reduce the SMS spams in developing nations like India. We use crowd-sourcing approach, apply machine learning techniques and keep the user preferences in our solutions. We are currently evaluating the effectiveness of the system in real-world among some volunteers (thanks for their time and efforts!).
Due to exponential increase in use of Short Message Service (SMS) over mobile phones in developing countries, there has been a burst of spam SMSes. The main goal for this research is to build algorithms and solutions to reduce the SMS spams in developing nations like India. We use crowd-sourcing approach, apply machine learning techniques and keep the user preferences in our solutions. We are currently evaluating the effectiveness of the system in real-world among some volunteers (thanks for their time and efforts!).
Dataset
If you are interested in sharing your SMS spams with us, please send them to +91 8826068429. Visit our Facebook page for more on our Dataset.
Relevant publications
Yadav, K., Kumaraguru, P., Goyal, A., Gupta, A., and Naik, V. Smsassassin : Crowdsourcing driven mobile-based system for sms spam filtering. Accepted at HotMobile (2011). Author’s version
Core members
Kuldeep Yadav, Ph.D. Student (Lead student)
Rushil Khurana, UG, IIIT-Delhi
Prof. Ponnurangam Kumaraguru
Prof. Vinayak Naik
Visiting students
Dipesh Kumar Singh, UG student, Sikkim Manipal Institute of Technology
Past members
Atul Goyal, UG student, IIIT-D
Ashish Gupta, UG student, IIIT-D
In News (selected ones)
Crowdsourced software could stop SMS spam (New Scientist)
We were on Google’s Sci/Tech. homepage for a few hours on March 7, 2011
Now ‘Kill’ that unwanted SMS (Mid-day)
If you are interested in knowing more or helping us with the research please write to pk [dot] guru [at] iiit [dot] ac [dot] in
Sponsors
While passwords, by definition, are meant to be secret, recent trends in the Internet usage have witnessed an increasing number of people sharing their email passwords for both personal and professional purposes. As sharing passwords increases the chances of your passwords being compromised, leading websites like Google strongly advise their users not to share their passwords with anyone. To cater to this conflict of usability versus security and privacy, we introduce ChaMAILeon, an experimental service, which allows users to share their email passwords while maintaining their privacy and not compromising their security. ChaMAILeon provides users with a unique capability to define access control on their emails. Now you can control who can see which emails and who can send emails to whom from your account, by having multiple passwords for your email. The service is already up and running! You can access it at the URL mentioned below.
URL
http://precog.iiitd.edu.in/chaMAILeon
Technical Report
Dewan P., Gupta M., Kumaraguru P., ChaMAILeon: Simplified email sharing like never before, IIITD-TR-2012-003
Core Team
Prateek Dewan, Ph.D. Scholar (Lead student)
Mayank Gupta, UG, Delhi College of Engineering
Prof. Ponnurangam Kumaraguru
Past Members
Sheethal Shreedhar, UG, NIT-Surathkal
 Online security attacks are a growing concern among Internet users.
Currently, the Internet community is facing three types of security
attacks: physical, syntactic, and semantic. Semantic attacks take
advantage of the way humans interact with computers or interpret
messages. There are three major approaches to countering semantic
attacks: silently eliminating the attacks, warning users about the
attacks, and training users not to fall for the attacks. The existing
methods for silently eliminating the attack and warning users about
the attack are unlikely to perform flawlessly; furthermore, users are
the weakest link in these attacks, it is essential that user training
complement other methods. Most existing online training methodologies
are less successful because: (1) organizations that create and host
training materials expect users to proactively seek out such material
themselves; (2) these organizations expect users to have some
knowledge about semantic attacks; and (3) the training materials have
not been designed with learning science principles in mind.
Online security attacks are a growing concern among Internet users.
Currently, the Internet community is facing three types of security
attacks: physical, syntactic, and semantic. Semantic attacks take
advantage of the way humans interact with computers or interpret
messages. There are three major approaches to countering semantic
attacks: silently eliminating the attacks, warning users about the
attacks, and training users not to fall for the attacks. The existing
methods for silently eliminating the attack and warning users about
the attack are unlikely to perform flawlessly; furthermore, users are
the weakest link in these attacks, it is essential that user training
complement other methods. Most existing online training methodologies
are less successful because: (1) organizations that create and host
training materials expect users to proactively seek out such material
themselves; (2) these organizations expect users to have some
knowledge about semantic attacks; and (3) the training materials have
not been designed with learning science principles in mind.
The goal of this work was to show that computer users trained with an
embedded training system – one grounded in the principles of learning
science – are able to make more accurate online trust decisions than
users who read traditional security training materials, which are
distributed via email or posted online. To achieve this goal, we focus
on "phishing," a type of semantic attack. We have developed a system
called "PhishGuru" based on embedded training methodology and learning
science principles. Embedded training is a methodology in which
training materials are integrated into the primary tasks users perform
in their day-to-day lives. In contrast to existing training
methodologies, the PhishGuru shows training materials to users through
emails at the moment ("teachable moment") users actually fall for
phishing attacks.
URL
http://www.wombatsecurity.com/phishguru
PhishGuru is currently being commercialized by Wombat
Security Technologies.
 As another implementation of phishing training, we used learning
science principles to develop Anti-Phishing Phil, an educational game.
Phil was designed to train users about phishing attacks, motivating
them to learn by embedding training into a fun activity. The highly
interactive nature of the game allows it to teach users to distinguish
legitimate links from fraudulent ones; it also provides users with
immediate opportunities to practice this procedure multiple times.
Anti-Phishing Phil complements PhishGuru by providing an entertaining
platform for the rapid repetition and feedback needed to teach more
difficult anti-phishing procedures.
As another implementation of phishing training, we used learning
science principles to develop Anti-Phishing Phil, an educational game.
Phil was designed to train users about phishing attacks, motivating
them to learn by embedding training into a fun activity. The highly
interactive nature of the game allows it to teach users to distinguish
legitimate links from fraudulent ones; it also provides users with
immediate opportunities to practice this procedure multiple times.
Anti-Phishing Phil complements PhishGuru by providing an entertaining
platform for the rapid repetition and feedback needed to teach more
difficult anti-phishing procedures.
URL
http://www.wombatsecurity.com/antiphishingphil
Anti-Phishing Phil is currently being commercialized by Wombat
Security Technologies.